The following high-level model illustrates layered segmentation, identity-bound access, and compartmentalized infrastructure domains.
The following high-level model illustrates layered segmentation, identity-bound access, and compartmentalized infrastructure domains.
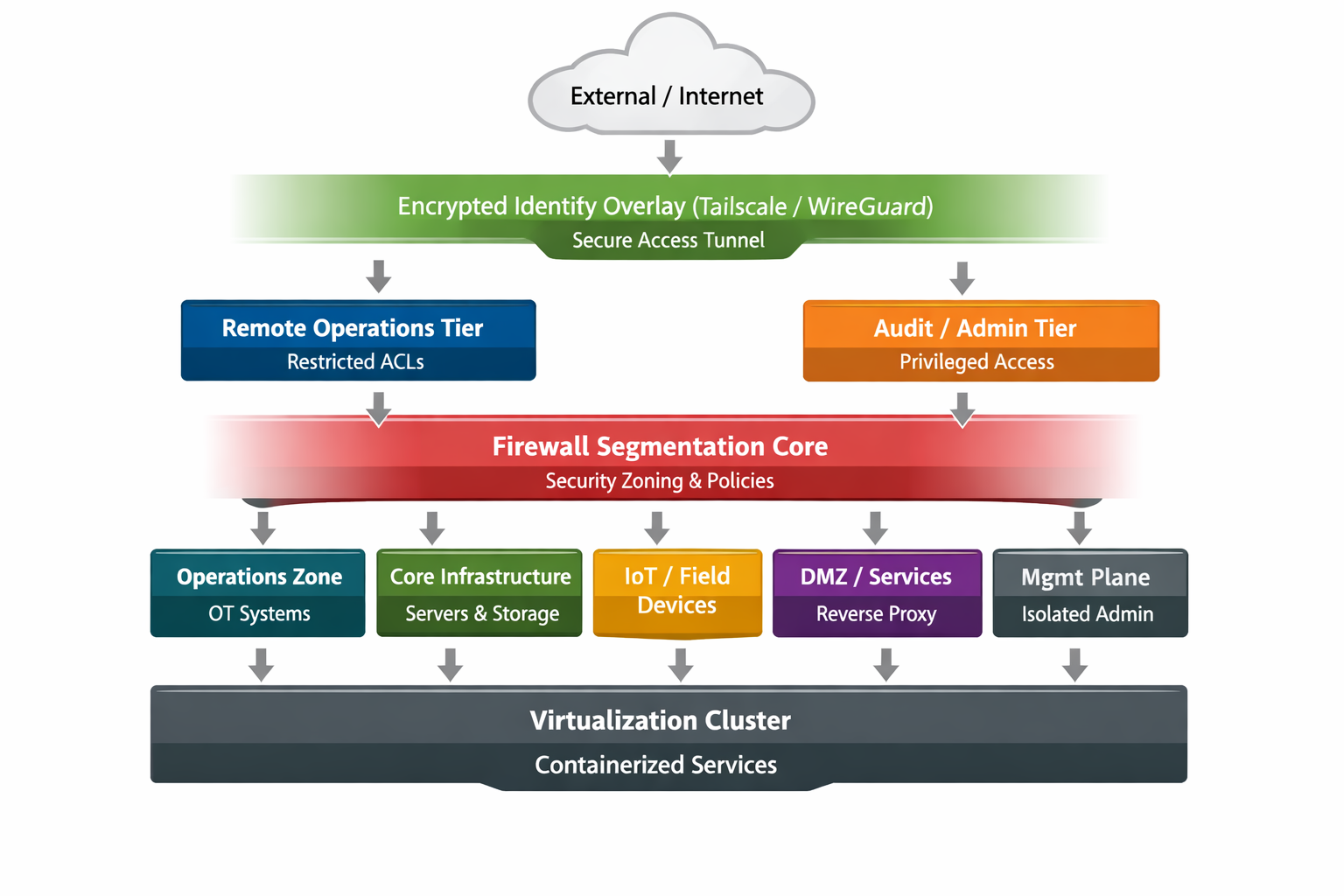
Each horizontal boundary represents a security enforcement layer:
Capabilities:
No single layer is trusted in isolation.
Untrusted environment. No direct administrative access permitted.
Implemented via Tailscale (WireGuard-based).
Implemented using OPNsense.
Clustered compute environment using Proxmox.
Runtime isolation using Docker.
If an adversary compromises:
Example:
Scenario: Field IoT device compromise
Result:
This demonstrates deterministic containment, not theoretical segmentation.